Ideation sections have been created for customers to engage with us by discussing and promoting ideas and improvements relating to Lenovo's products and services Decry pt the EFS encrypted file a bit hard way Step 1 Login with userid "malicioususer" Step 2 In our scenario we need to extract keys for user "admin" who has encrypted the confidential file For this, we need to navigate to "C\Users\Gentil Kiwi\AppData\Roaming\Microsoft\SystemCertificates\My\Certificates\Size 416MB Size on disk
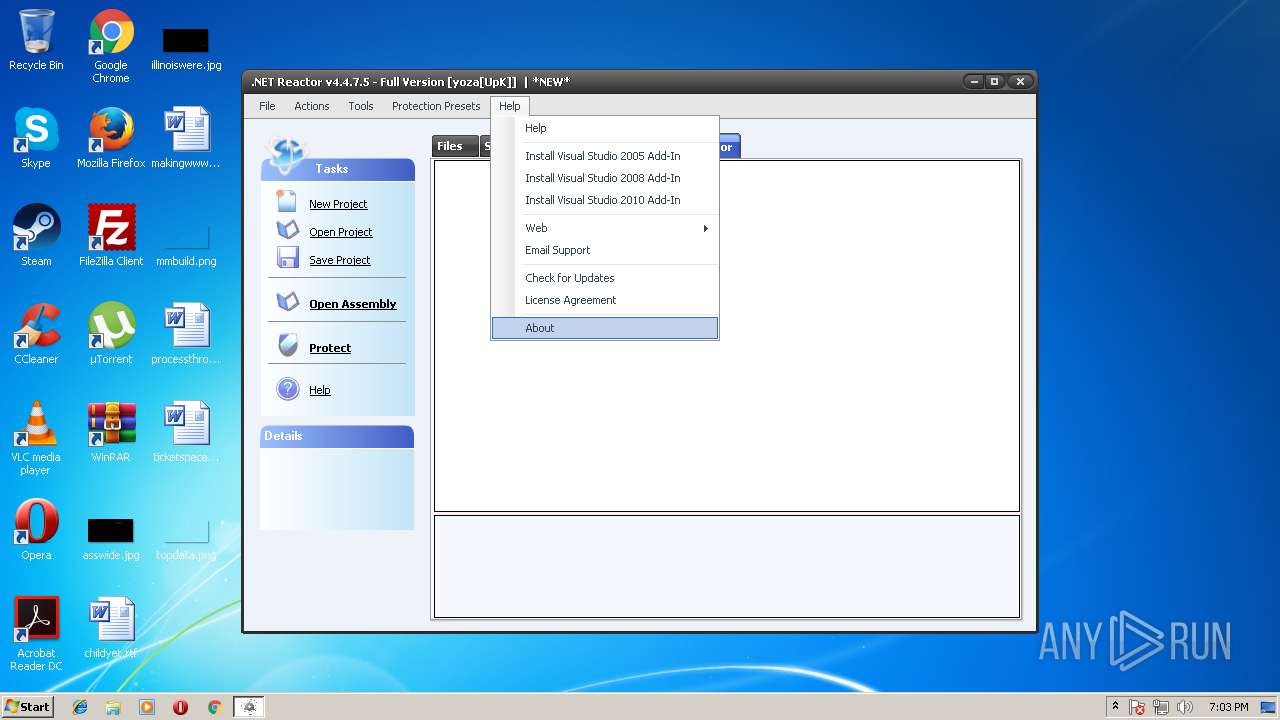
79f190a51af8a463f13ddd5acf7ba2adfb8e231b37c5ea62b Any Run Free Malware Sandbox Online
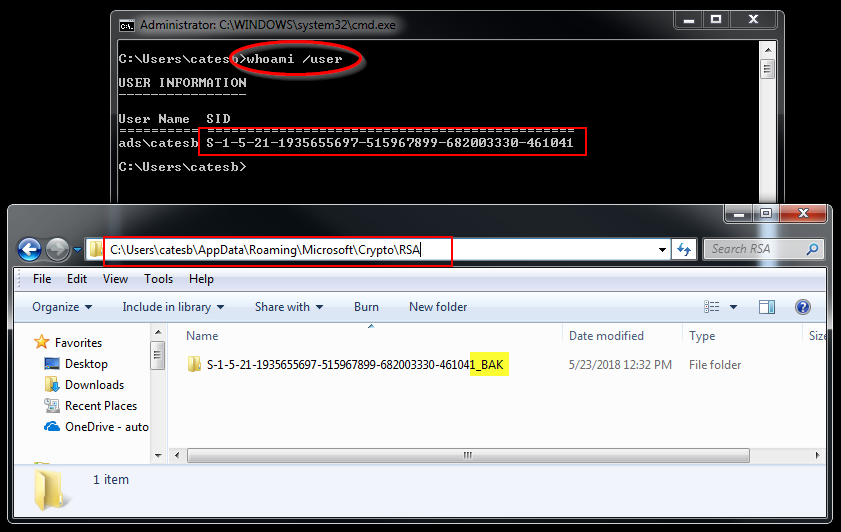
Appdata roaming microsoft crypto rsa s-1-5-21
Appdata roaming microsoft crypto rsa s-1-5-21- Hello there Ive just did my first scan on my sister laptop cause she never scanned her laptop before and getting some malware Can you please help me interpret them and if they are actually dangerous or notMalwarebytes AntiMalwarewwwmalwarebytesorg Scan Date Scan Time 1123 AMLo I found a file in C\Users\BESTChR\Appdata\Roaming\Microsoft\Crypto\RSA\S1521 It's filename is 5550e7 It contains a few cryptic chars and "WinampKeyContainer"



Operational Guidance For Offensive User Dpapi Abuse Harmj0y
Is this safe ?C\Users\kabutor\AppData\Roaming\Microsoft\Crypto\RSA\ and C\Users\kabutor\AppData\Roaming\Microsoft\Protect\ To find out the master key we need and to decrypt the certificate we will use mimkatz, we ask the When running an "normal" application as Admin (right click > Run as Admin) executing exactly the same code, a file is created at C\Users\ Username\AppData\Roaming\Microsoft\Crypto\RSA\S The certificate generated using the WIX custom action seems to not have a
ran ALOGENTSVCHOSTEXE, which tried to access C\USERS\RDCADMIN1\APPDATA\ROAMING\MICROSOFT\CRYPTO\RSA\SWhen searching a file or folder, specify a path with /pathC\Path\to\file\or\folder and optionally use /maxBytes to specify the number of bytes to read from each file (default 1024 bytes) The command will read the bytes from the beginning of the file and search for DPAPI blobs Hi, I want to remove a certificate from my certificate store Although the certificate is removed, its associated private key is not deleted It can be seen in the C\Users\xxx\AppData\Roaming\Microsoft\Crypto\RSA\S1521xxx folder How to cleanly remove a certificate ?
Our commitment to the environment Lenovo is committed to environmental leadership from operations to product design and recycling solutions See our Sustainability ReportThe case of accidentally deleted user certificates Sometimes users accidentally delete their certificates from personal store After that users are not able to perform certificatebased tasks, ie decrypt files or mail, sign data and authenticate Some organizations implement Key Archival for certificate and private key recovery DPAPIindepth with tooling standalone DPAPI The Microsoft Data Protection Application Programming Interface, or DPAPI for short, is a Windows API tool for developers to enable them to store sensitive data in a way that it is encrypted but still decryptable It has been around since Windows 00 which makes it more or less ancient in computer
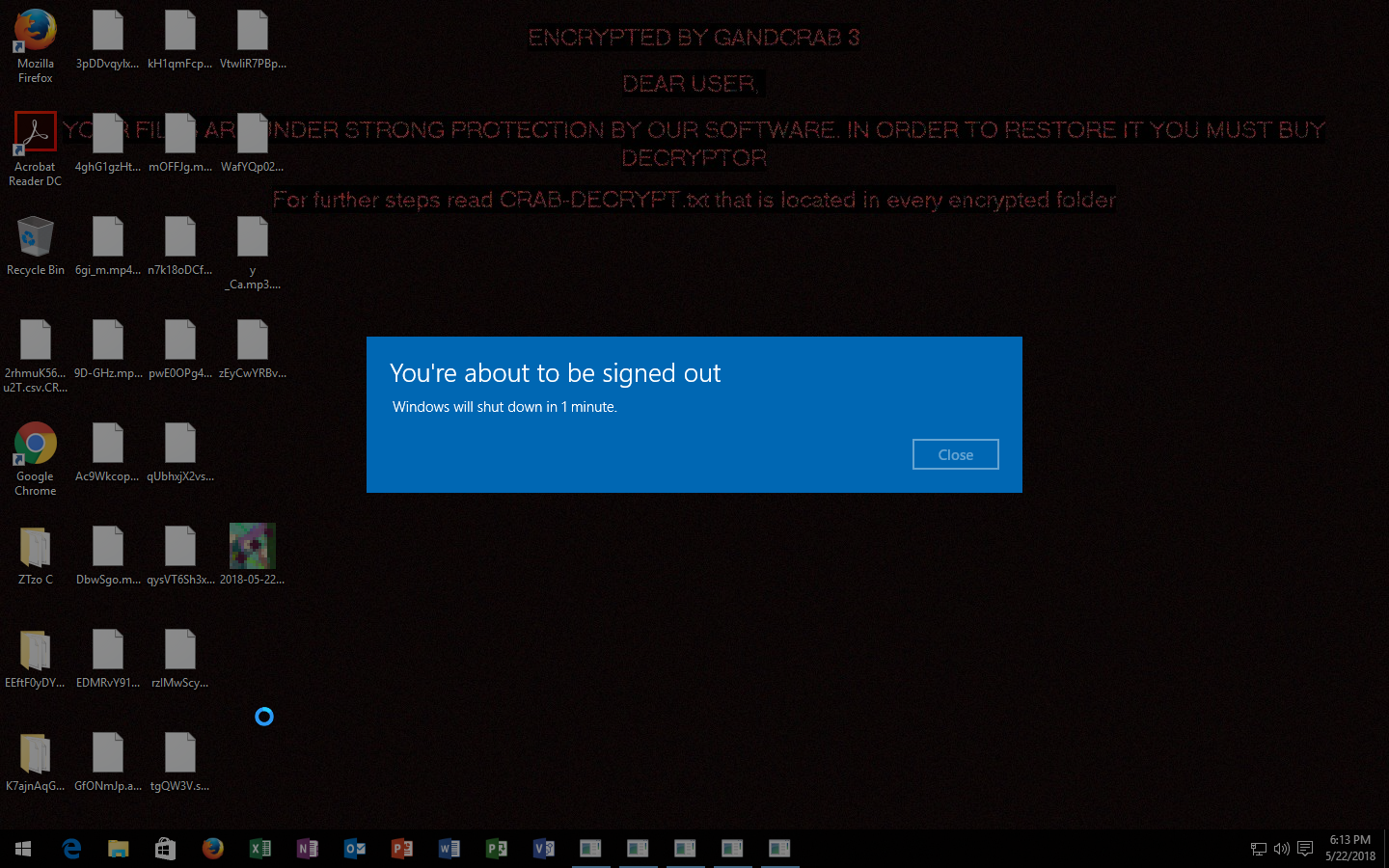



Gandcrab Ransomware V3 0 1 Grouped Behavior



Operational Guidance For Offensive User Dpapi Abuse Harmj0y
Previously on CQLabs This article is a continuation of a previous one, called #CQLabs 5 – DSInternals PowerShell Module Introduction One of the lesser known features of Active Directory (AD) is called Credential RoamingWhen enabled, it synchronizes DPAPI Master Keys, user certificates (including the corresponding private keys) and even saved passwords between We use an application that uses NET to decrypt data "Every now and then" the application stops with and error related to RSA The fix we have is to delete the files in c\ C\Users\\AppData\Roaming\Microsoft\Crypto\RSA\S1521AppData\Roaming\Microsoft\Crypto\RSA\S\ Your directory may have other random numbers after /RSA/ Right Click the picture below to open the image in a new tab Debugging System The sample was tested and debugged on (x86) – 32 Bit, Windows 7 Professional




Penetration Testing By Expl0i13r Decrypting Efs Encrypted Files



All Of The Possible Directories For Storing Temporary Files Either Do Not Exist Or Are Readonly When Launching Autocad Autocad Autodesk Knowledge Network
Access is denied macOS The operation can't be completed because you don't have permission to access some of the items The folder %AppData%\Roaming\Microsoft\Crypto\RSA (Example C\Users\qliksenseservices\AppData\Roaming\Microsoft\Crypto\RSA\S)(certificate Hi, Based on my tests, we can use Certutil –key command




Ransomware Breakout



Is It Safe To Delete The Files Found In Rsa Crypto
Hello @Charbo Many thanks for posting on the Community I've reviewed your Service Request and have left a note for the Owner of the case with the details however here a modified version of what I can see from the data supplied BTW, yesterday makecert put the newly generated certificates into directory "C\Users\gz\AppData\Roaming\Microsoft\Crypto\RSA\S", today it put the certificate into "C\ProgramData\Microsoft\Crypto\RSA\MachineKeys" strange, thats why yesterday it workedIs it related to crypto Mining ?




Rabid Trojan Of The Week Cybercrypto




Att Ck Evaluations
If the operating system (OS) can be loaded (either normally or in safe mode), download DrWeb Security Space and run a full scan of your computer and removable media you use type C\Users\m0chan\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadline\ConsoleHost_historytxt cat (GetPSReadlineOption) HistorySavePath cat (GetPSReadlineOption) HistorySavePath sls passw View Connected Drives net use wmic logicaldisk get caption, description GetPSDrive When I load a certficate into the "Current User" store, it puts a private key file here C\Users\ userIDA\AppData\Roaming\Microsoft\Crypto\RSA\S1521xxx\pkfileqreflr8029r When I load a certficate into the "Local Machine" store using a different UserIDB, I don't see this path at all C\Users\ userIDB\AppData\Roaming\Microsoft\Crypto there is no \Crypto



2




Ransomware Breakout
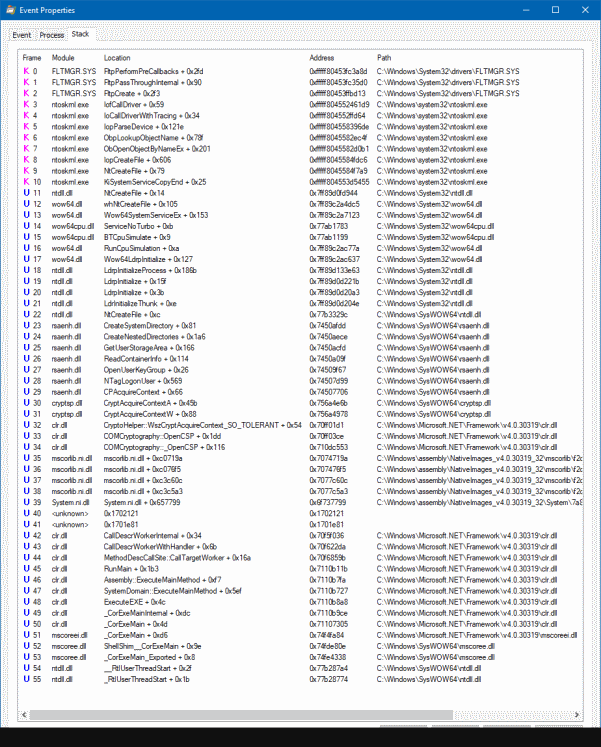
For 5058 (S, F) Key file operation Typically this event is required for detailed monitoring of KSPrelated actions with cryptographic keys If you need to monitor actions related to specific cryptographic keys ( "Key Name") or a specific "Operation", such as "Delete key file", create monitoring rules and use this event as anThe amount of files in C\ProgramData\Microsoft\Crypto\RSA\S1518 is abnormally high Cause Whenever a signature is placed into a document, and the biometric data is encrypted with the encryption key, SignDoc SDK is using the Windows Crypto Api for encrypting the biometric dataC\Users\Nd9E1FYi\AppData\Local\Microsoft\Windows\PowerShell\CommandAnalysis\PowerShell_AnalysisCacheEntry_0acb7fb46d680e601ae18 Modified File Stream




Ransomware Breakout




The Case Of Accidentally Deleted User Certificates Pki Solutions Inc
C\Users{user}\AppData\Roaming\Microsoft\SystemCertificates\My\Keys Certs show and claim to have private keys under properties, but export shows the key cannot be found, and when using the cert to access a Bank web site, the SSL handshake fails Wasn't sure so put keys here also C\Users{user}\AppData\Roaming\Microsoft\Crypto\RSA\S1521 "C\Windows\System32\WScriptexe" "C\Users\admin\AppData\Local\Temp\subfolder\ilamavbs" Path C\Windows\System32\WScriptexe Indicators Parent process malwareexe User admin Integrity Level MEDIUM Exit code 0 Version Company Microsoft Corporation Description Microsoft ®" C\Users\hgupt\AppData\Roaming\Microsoft\Crypto\RSA\S "And inside these folders it contains some weird files ( extension of these files are >> sys ) Why these files and folders are there ?




Threat Roundup For March 13 To March



2
On the January patchday, the vulnerability CVE0601 discovered by the NSA and reported to Microsoft became public As a reminder, there is a spoofing vulnerability CVE0601 in the Crypt32dll library (CryptoAPI) that could be exploited by attackers An attacker could use a spoofed codesigning certificate to sign a maliciousJoe Sandbox Cloud Basic Interface C\Users\user\AppData\Roaming\Microsoft\Crypto\RSA\S\8cdde80db2e906b7cd06 Posted Hi, I was looking at the Scheduler section in the Operating System protion of Speccy and there's some unusual information that I don't recognize It shows relevant info on stuff I have scheduled updates for, like windows update, spyware, and anti virus, but this one I don't recognize and it just started on of



2



Antivirus10 Bloodhound Exploit 213 Dwh Tmp Solved Virus Spyware Malware Removal
It doesn't have a file extension AppData\Roaming\Microsoft\Crypto\RSA\S 1000\eadbb38b859a5ac130a8_05b9da15ee4a4c9f952bd6b8a1b The Thanks for the note When I go to the following directory \AppData\Roaming\Microsoft\Protect\ there is one directory (S) opening that directory says 'No Files' However when I do properties on the directory it tell me there are 934,000 files in it? The certificate's physical file location should now be within the directory "C\ProgramData\Microsoft\Crypto\RSA\MachineKeys\" and this can be verified by using the FindPrivateKey app VI Once we are confident that our certificate is both, in the correct store location and in the correct physical file location then we can apply the



2



Dpapi In Depth With Tooling Standalone Dpapi Industrial Security Research Group
What are these folders do ?Saya mulai percaya mereka berada di AppData \ Roaming \ Microsoft \ Protect \ S1521 \ atau AppData \ Roaming \ Microsoft \ Crypto \ RSA \ S1521 \ tetapi saya tidak yakin bagaimana cara menggunakan file di folder itu Juga, karena SID saya telah berubah, apakah saya dapat menggunakannya?C\ProgramData\Microsoft\Crypto\RSA\MachineKeys if deleting from localMachine store and from C\UsersUsername\AppData\Roaming\Microsoft\Crypto\RSA\S if deleting from CurrentUser store




Penetration Testing By Expl0i13r Decrypting Efs Encrypted Files
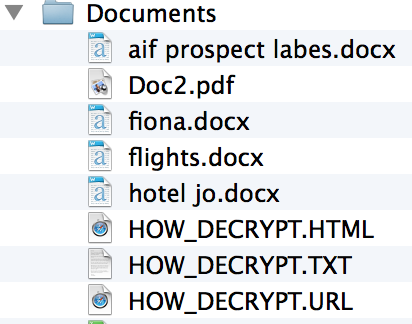



Cryptodefense Infection Some Lessons Learned
The first thing I always check is ERRORLOG and here is what I found there spid18s Error , Severity 16, State 1 Windows users may unintentionally enable EFS encryption (even from just unpacking a ZIP file created under macOS), resulting in errors like these when trying to copy files from a backup or offline system, even as root Windows File Access Denied;Antivirus is blocking the process Open operating system event viewer start > run > Eventvwr check for any entry which is blocking the cmAppexe




Restore Efs Encrypted Files After Reinstalling The System Programmer Sought




Restore Efs Encrypted Files After Reinstalling The System Programmer Sought
Next, we'll need the keys from %appdata% directory, located in the following path C\Users\USERNAME\AppData\Roaming\Microsoft\Protect\SID The SID stands for Security Identifier, for example S Additionally, note that all the files inside this folder are hidden, so use dir /a to list them



6a44af7ac01afc6ffe4df30d8a7caeb816d967b Any Run Free Malware Sandbox Online



Appdata Roaming Microsoft Crypto Rsa



11e6aca8e6c046cb721eeb5c72c5ef03cb5936c60df6fddc Any Run Free Malware Sandbox Online




Lync Cant Sign In To Lync There Was A Problem Acquiring A Personal Certificate Required To Sign In Solutions By Shayatik Com




79f190a51af8a463f13ddd5acf7ba2adfb8e231b37c5ea62b Any Run Free Malware Sandbox Online
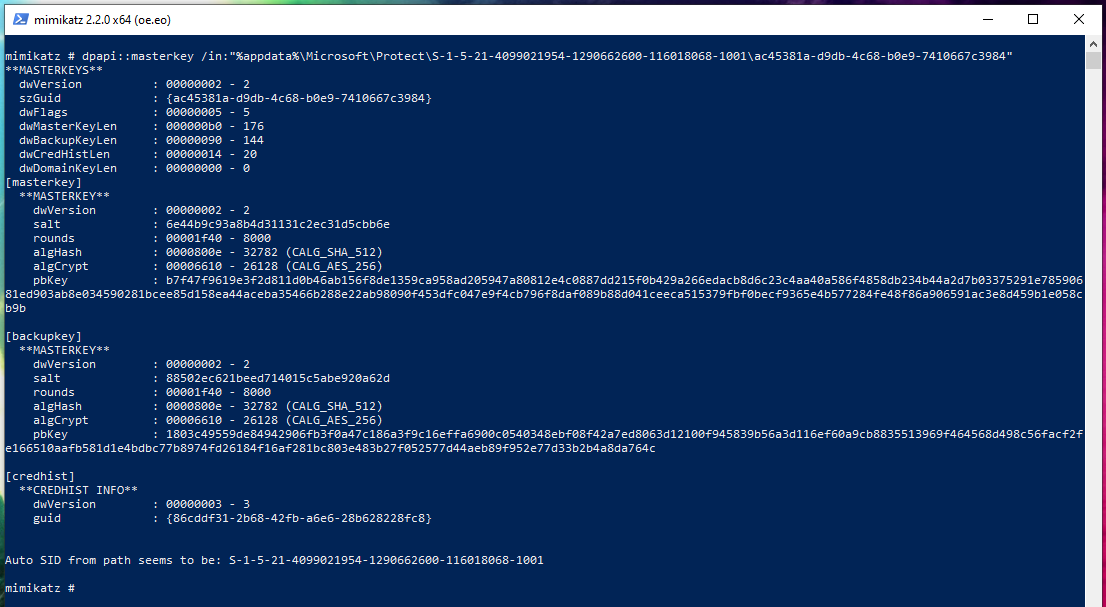



How To Decrypt Stored Windows Passwords Using Mimikatz And Dapa Ethical Hacking And Penetration Testing
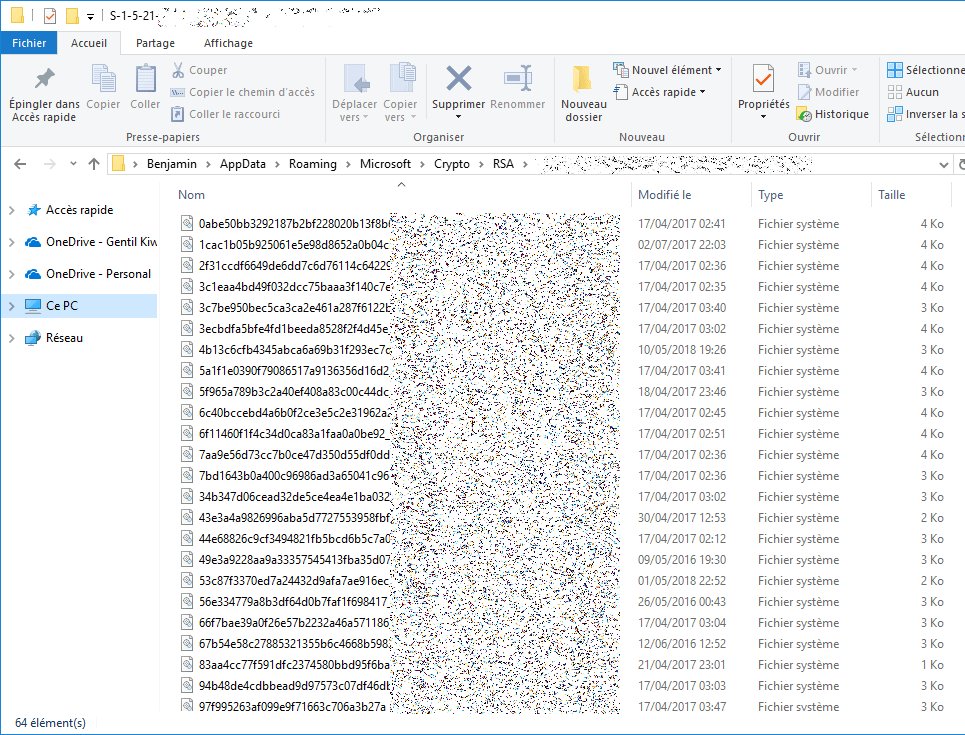



Benjamin Delpy Gentle Reminder When You Delete Certificates On Windows It Does Not Delete Associated Private Keys On The Disk Take A Look In Appdata Microsoft Crypto Rsa Of All Users




Dpapi Extracting Passwords Hacktricks
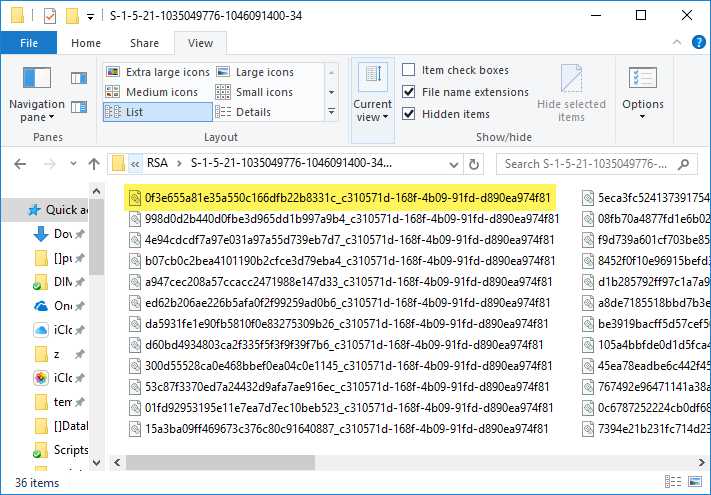



Cryptographic Key Containers Cryptography In Net Succinctly Ebook



Crsvc 8778 Machine Key Accumulation Results In Low Disk Space On Workspace One Uem Application Servers 553 Vmware Kb




I Still Can T Open Encrypted Files After Importing Pfx Practical Manually Recover Efs Encrypted Files Programmer Sought
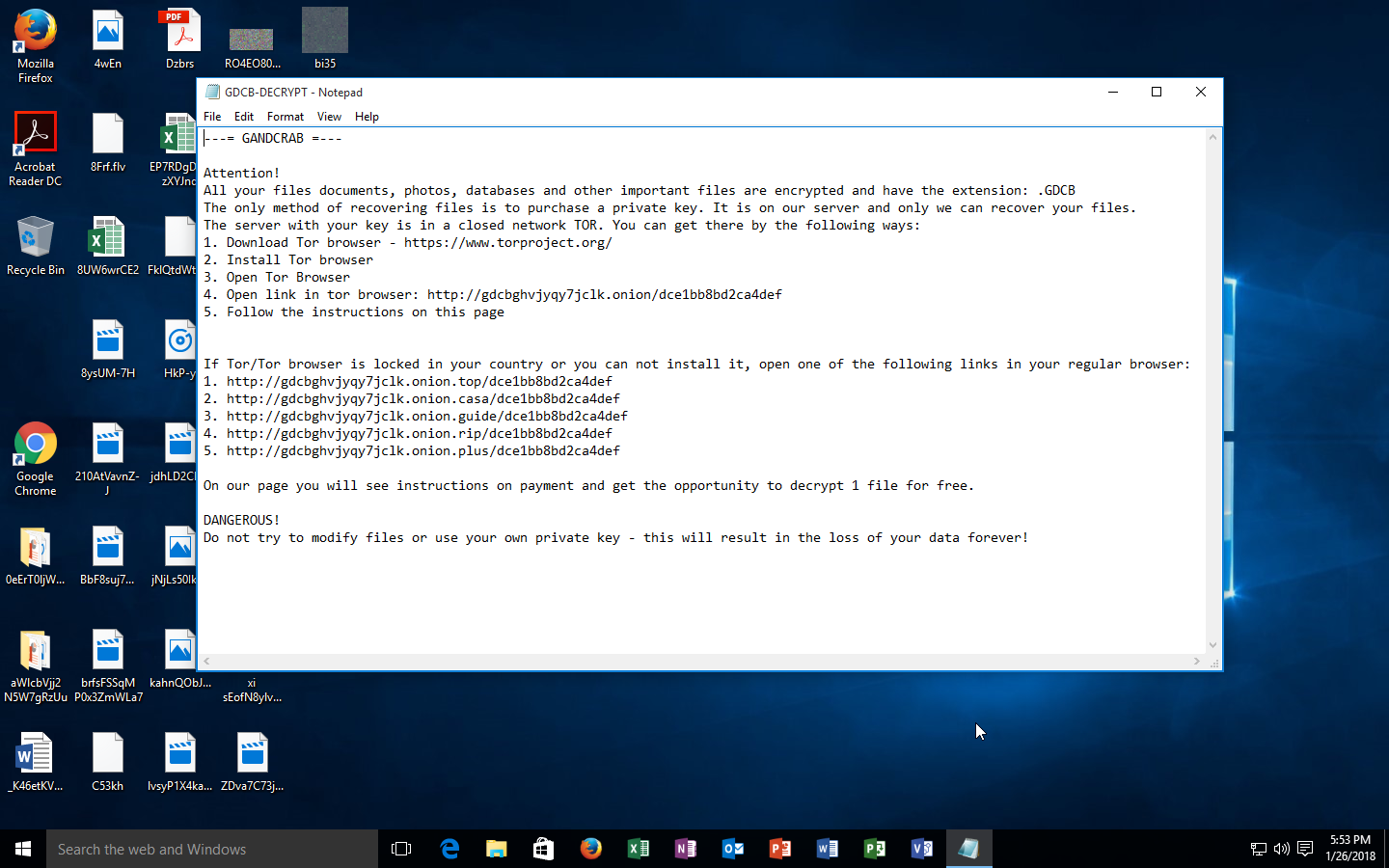



Gandcrab Ransomware Files




When Do Files Get Written To Appdata Roaming Microsoft Crypto Rsa Microsoft Q A




Temporare Files In Programdata Microsoft Crypto Rsa S 1 5 18 Directory Kofax



Computer Infected Resolved Virus Spyware Malware Removal




Cisco Talos Intelligence Group Comprehensive Threat Intelligence Threat Roundup For June 21 To June 28



Many Errors On Client Backup With Retrospect 7 7 Server Sbs And Multi Server Retrospect Forum
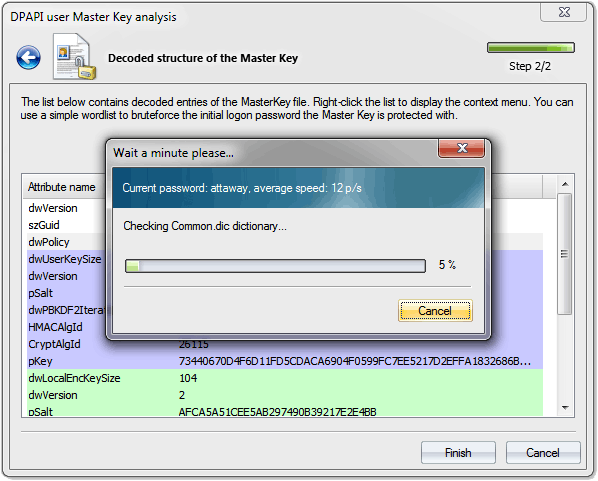



Dpapi Secrets Security Analysis And Data Recovery In Dpapi




Htb Helpline Kali 0xdf Hacks Stuff




Cisco Talos Intelligence Group Comprehensive Threat Intelligence Threat Roundup For June 21 To June 28




Hermes Ransom Help Support Topic Decrypt Information Html Ransom Note Ransomware Help Tech Support




Pc No Connection To Matchmaking Services Possible Solution Nms Beyond Bugs Issues Etarc Community




Hackthebox Helpline Pentest Diaries



Is It Safe To Delete The Files Found In Rsa Crypto



Signing Certificate Has Not Private Key Issue 2677 Identityserver Identityserver3 Github



Encryption Paired Keys




Dpapi Extracting Passwords Hacktricks



Win32 Small Ca Virus Solved Virus Spyware Malware Removal




Hackthebox Helpline Pentest Diaries



Gandcrab Ransomware V4 1 Files
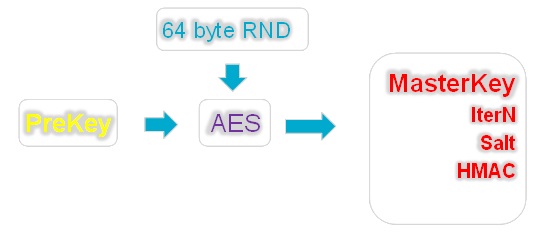



Secrets Dpapi Or Dpapi For Pentesters Sudo Null It News
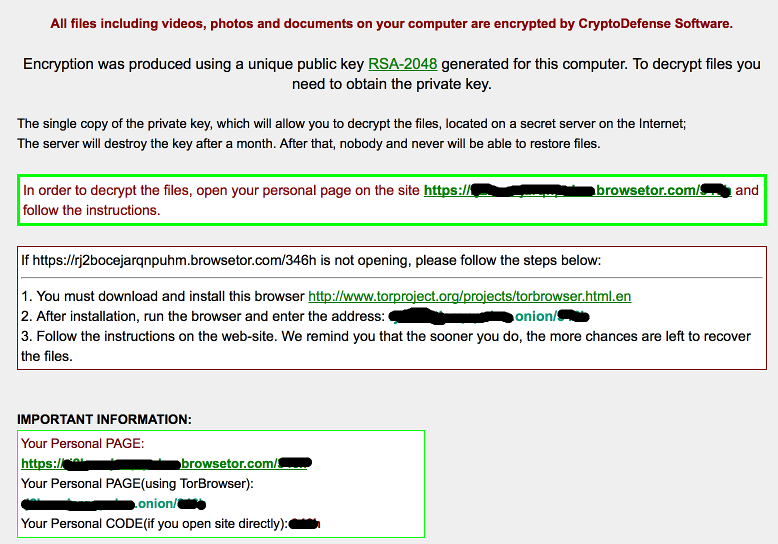



Cryptodefense Infection Some Lessons Learned




Machinekeys Folder Fills Up Quickly




Three S A Crowd New Trickbot Emotet Ryuk Ransomware By Littl3field Littl3field




Ransomware Breakout




Ransomware Breakout




Dpapi Extracting Passwords Hacktricks




Showcase See Top Companies Building With Meteor




Fixed Skype Certificate Error Quick Guide




Secrets Dpapi Or Dpapi For Pentesters Sudo Null It News




I Still Can T Open Encrypted Files After Importing Pfx Practical Manually Recover Efs Encrypted Files Programmer Sought
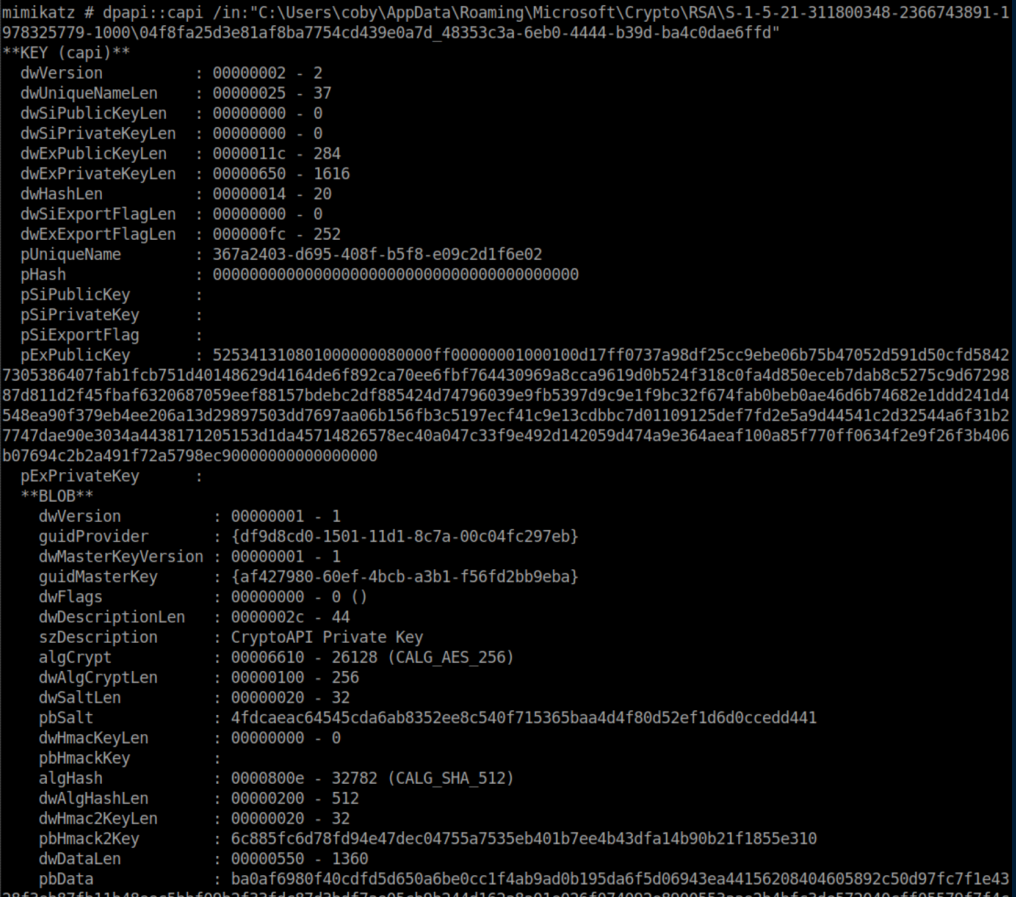



Hackthebox Writeup Re
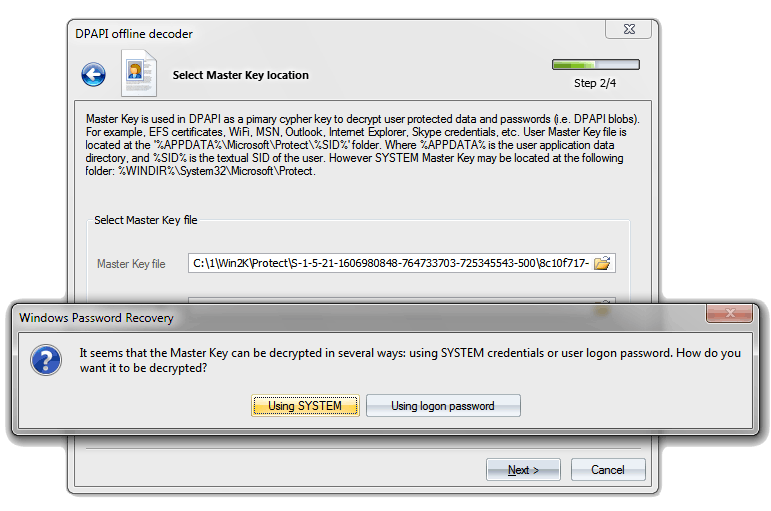



Dpapi Secrets Security Analysis And Data Recovery In Dpapi




Cryptodefense Ransomware Support And Help Topic How Decrypt Txt Page 4 General Security




Sql Server Startup Error Severity 16 Initializing The Fallback Certificate Failed With Error Code 1 State Sql Authority With Pinal Dave




Trickbot Update Brief Analysis Of A Recent Trickbot Payload Sentinellabs



Every Time System Net Security Tests Functionaltests Runs Some Disk Space Gets Eaten Up Permanently Issue 175 Dotnet Runtime Github




I Still Can T Open Encrypted Files After Importing Pfx Practical Manually Recover Efs Encrypted Files Programmer Sought



Pythonforwindows Certificate Py At Master Hakril Pythonforwindows Github




Htb Helpline Kali 0xdf Hacks Stuff



Coolwww And Cycbot B Virus Spyware Malware Removal




Invalid Provider Type Specified Cryptographicexception When Trying To Load Private Key Of Certificate Stack Overflow



Encryption Rsa And Nte Bad Keyset



Sha256 C9e3e02f7ff8c8b446b4a12d93f646fefc48d3cb3841b2a3fcf54a8 Alienvault Open Threat Exchange



Gandcrab Ransomware V3 0 1 Grouped Behavior




When Opening A Query Script I Receive The Error Message The Query Script Is Corrupted Winshuttle




Restore Efs Encrypted Files After Reinstalling The System Programmer Sought



Sha256 153f1acb5b9fa100b1a863c25c1fb167a314a54a75adaf2c4feaaba Alienvault Open Threat Exchange



Heart Goes Out To 100 C Programdata Microsoft Crypto Rsa S 1 5 18 Eehelp Com
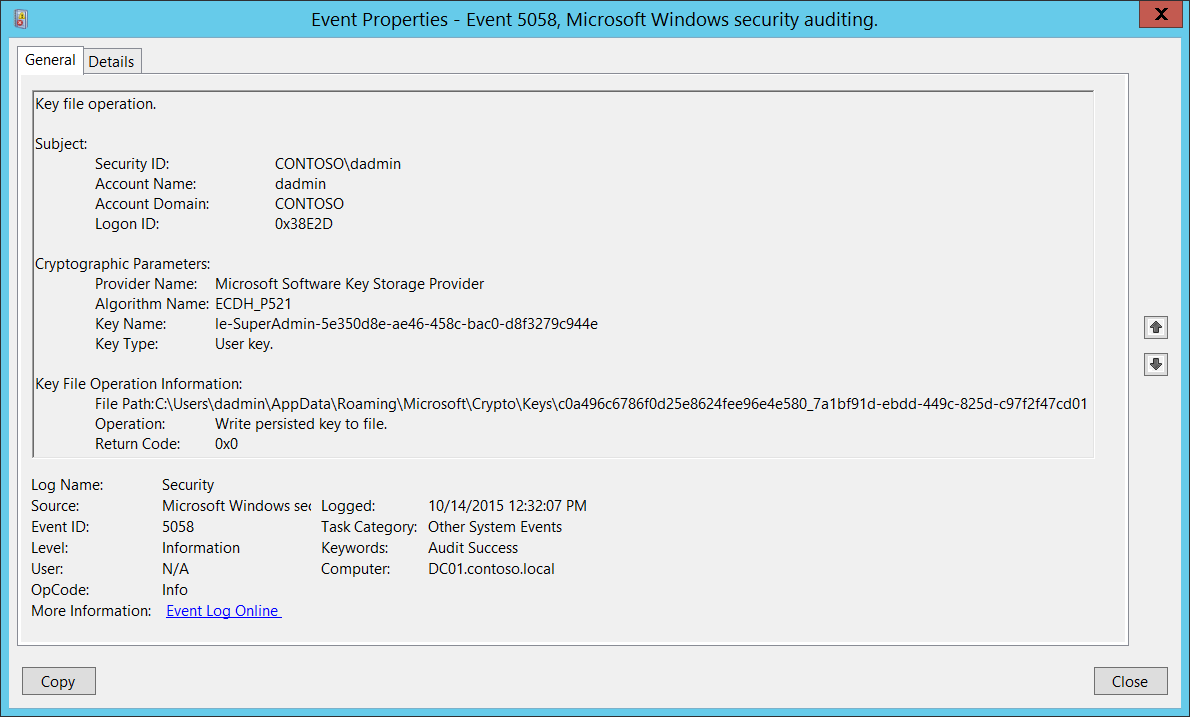



5058 S F Key File Operation Windows 10 Windows Security Microsoft Docs



How To Get The Certificate Key Container String
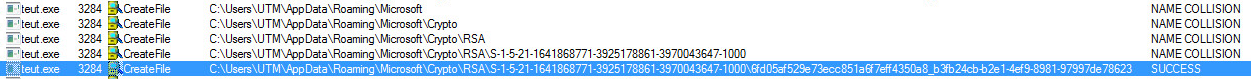



Trickbot Banking Variant Actively Spreading Sonicwall
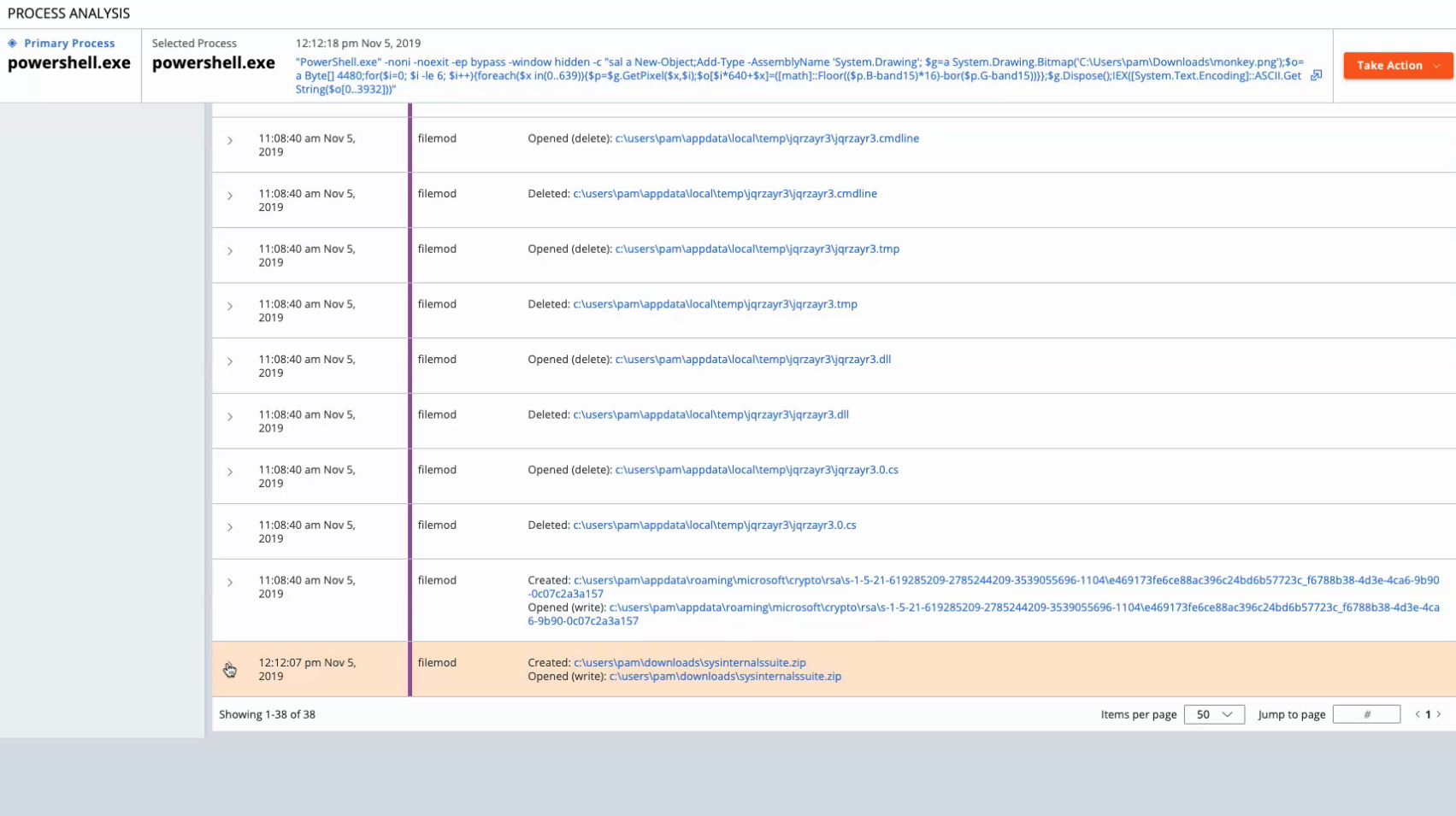



Att Ck Evaluations



2f125eaa11cfa562bbbffcff3c7eee463fccbaddab8eccbf Any Run Free Malware Sandbox Online




Restore Efs Encrypted Files After Reinstalling The System Programmer Sought




Secrets Dpapi Or Dpapi For Pentesters Sudo Null It News



How To Get The Certificate Key Container String




Some Stuff About Security 15




Dpapi Secrets Security Analysis And Data Recovery In Dpapi




Htb Helpline Kali 0xdf Hacks Stuff




Att Ck Evaluations




Smart Tokens And Pki Color Part 2 12 9 19 18 24 3 968 Public Key Certificate Backup



Coolwww And Cycbot B Virus Spyware Malware Removal




Pc No Connection To Matchmaking Services Possible Solution Nms Beyond Bugs Issues Etarc Community




How To Decrypt Stored Windows Passwords Using Mimikatz And Dapa Ethical Hacking And Penetration Testing




Dpapi Extracting Passwords Hacktricks
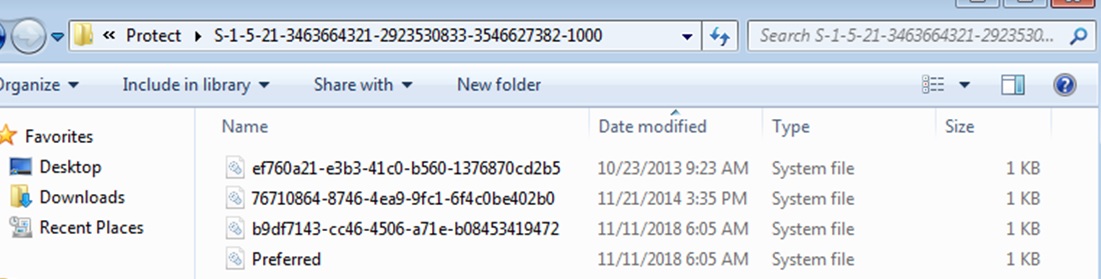



Secrets Dpapi Or Dpapi For Pentesters Sudo Null It News




Some Stuff About Security 15



0 件のコメント:
コメントを投稿